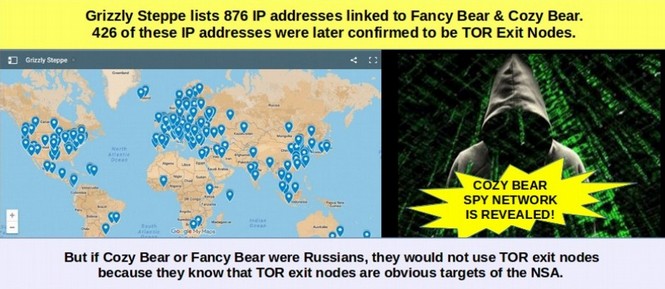
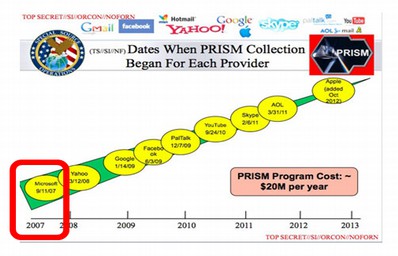
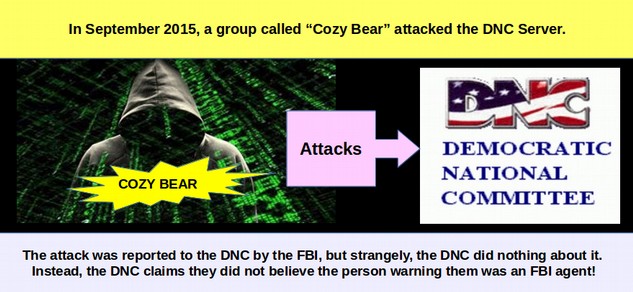
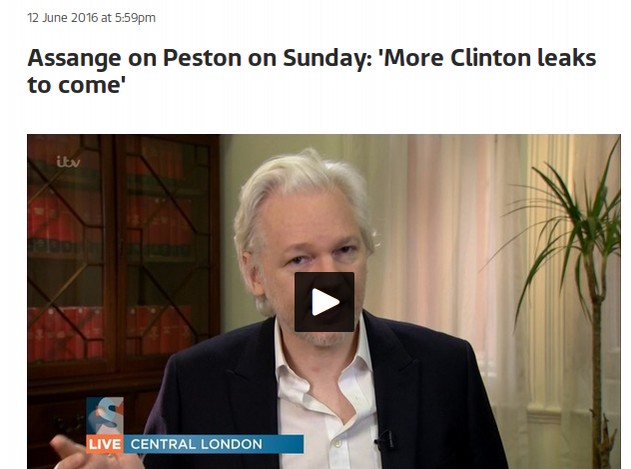
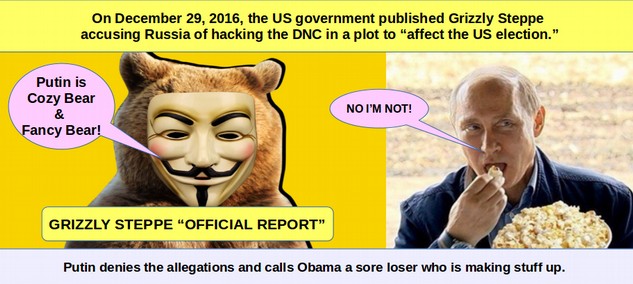
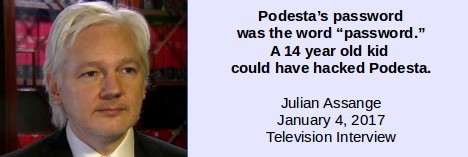
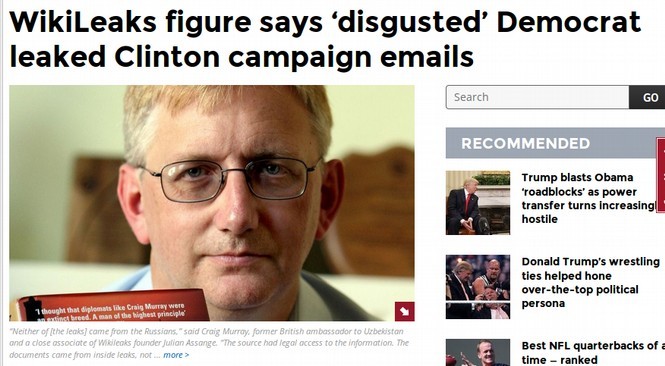
Connecting the Dots between Microsoft Backdoors, NSA Corruption and the Bitcoin Ponzi Scheme
David Spring M. Ed. December 2, 2013
Notes: The original version of this article was published on my old website Free Yourself From Microsoft and the NSA dot org on December 2 2013. Nearly one million people read this article as it was shared by groups around the world. It caused such a firestorm that I spent a huge amount of time answering emails about the article. I therefore took the article down a few years later. However, an edited version of this article was also posted on a website called Oped News dot com on December 5, 2013. It is still there at this link: http://www.opednews.com/articles/Connecting-the-Dots-betwee-by-David-Spring-Spying-131206-522.html
Here is the unedited version of the article: In the past three months since I published Free Yourself from Microsoft and the NSA, there has been a steady stream of increasingly shocking revelations about the extent of NSA spying in the US and around the world. NSA operatives have been caught spying on their wives and girlfriends. The NSA has also been caught spying on dozens of world leaders including Angela Merkel, the elected leader of Germany and the Pope in the Vatican, the leader of the Catholic Church. http://news.panorama.it/cronaca/papa-francesco-datagate
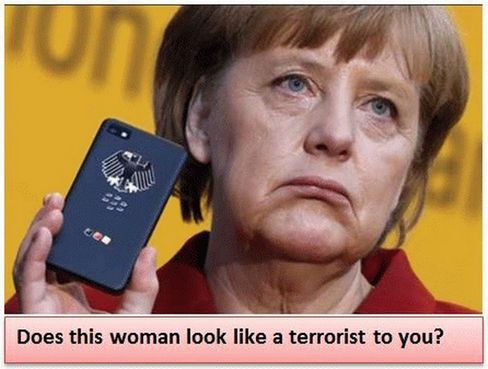
Clearly Angela Merkel and the Pope are not “terrorist threats.” In fact, the greatest threat to democracies around the world is the out of control lunatics pulling the strings at the NSA.
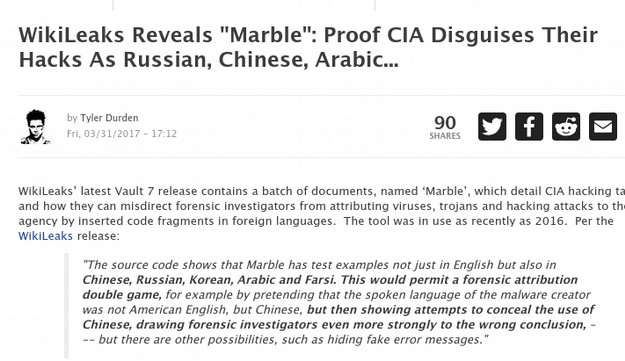
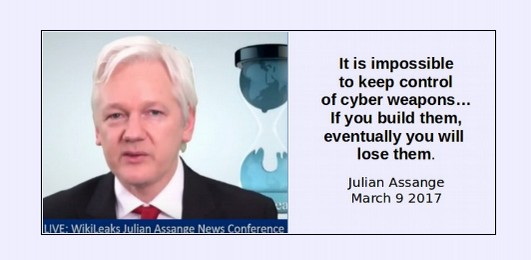
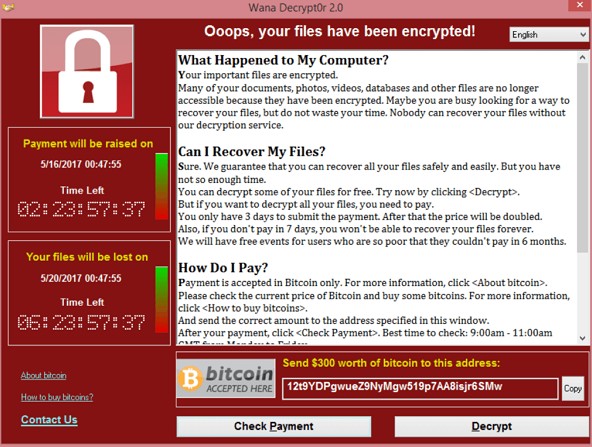
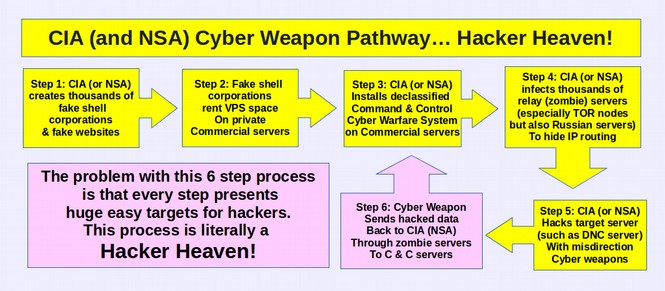
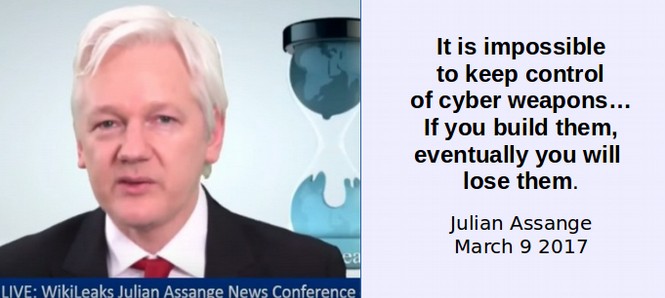
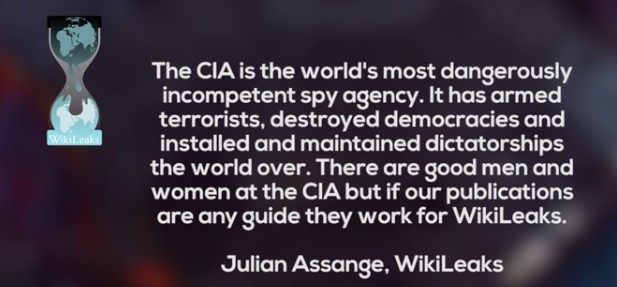
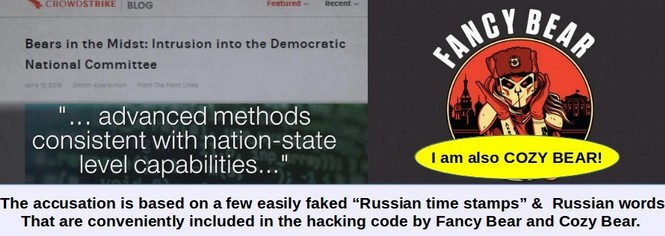
At the recent trial of hacker Jeremy Hammond, it was revealed that the NSA and FBI paid an informant named Sabu to help Jeremy Hammond hack into various government websites and computer systems all around the world. In November 2013, it was revealed that the NSA has hacked into more than 85,000 Windows computer networks around the world.
David Spring M. Ed. December 2, 2013
Notes: The original version of this article was published on my old website Free Yourself From Microsoft and the NSA dot org on December 2 2013. Nearly one million people read this article as it was shared by groups around the world. It caused such a firestorm that I spent a huge amount of time answering emails about the article. I therefore took the article down a few years later. However, an edited version of this article was also posted on a website called Oped News dot com on December 5, 2013. It is still there at this link: http://www.opednews.com/articles/Connecting-the-Dots-betwee-by-David-Spring-Spying-131206-522.html
Here is the unedited version of the article: In the past three months since I published Free Yourself from Microsoft and the NSA, there has been a steady stream of increasingly shocking revelations about the extent of NSA spying in the US and around the world. NSA operatives have been caught spying on their wives and girlfriends. The NSA has also been caught spying on dozens of world leaders including Angela Merkel, the elected leader of Germany and the Pope in the Vatican, the leader of the Catholic Church. http://news.panorama.it/cronaca/papa-francesco-datagate

Clearly Angela Merkel and the Pope are not “terrorist threats.” In fact, the greatest threat to democracies around the world is the out of control lunatics pulling the strings at the NSA.
At the recent trial of hacker Jeremy Hammond, it was revealed that the NSA and FBI paid an informant named Sabu to help Jeremy Hammond hack into various government websites and computer systems all around the world. In November 2013, it was revealed that the NSA has hacked into more than 85,000 Windows computer networks around the world.